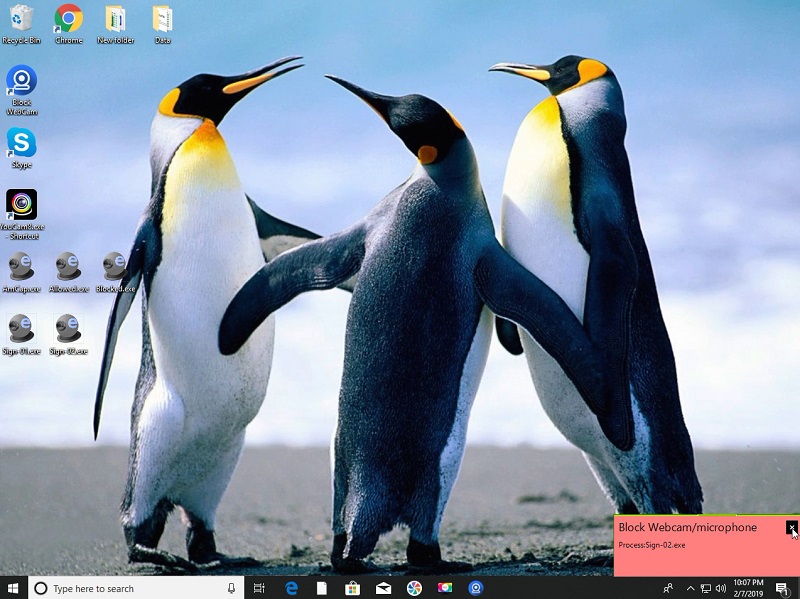
Block WebCam and microphone
The *Block Webcam and microphone* product allows only WebCam or Microphone to be used for the applications that are allowed. This helps prevent malware, Ransomware, etc. from leaking your personal information using your your WebCam or Microphone.

COVERT Pro
COVERT Pro - an innovative solution to ensure total privacy while working at the computer and protecting against tracking programs. Protecting against spyware programs by masking action of computer user.

DoNotSpy10
DoNotSpy10 is the world*s first antispy tool for Windows 10. Its straight-forward user interface allows you to manage how Windows 10 respects their privacy. Microsoft introduces many new *diagnostic* features with Windows 10.
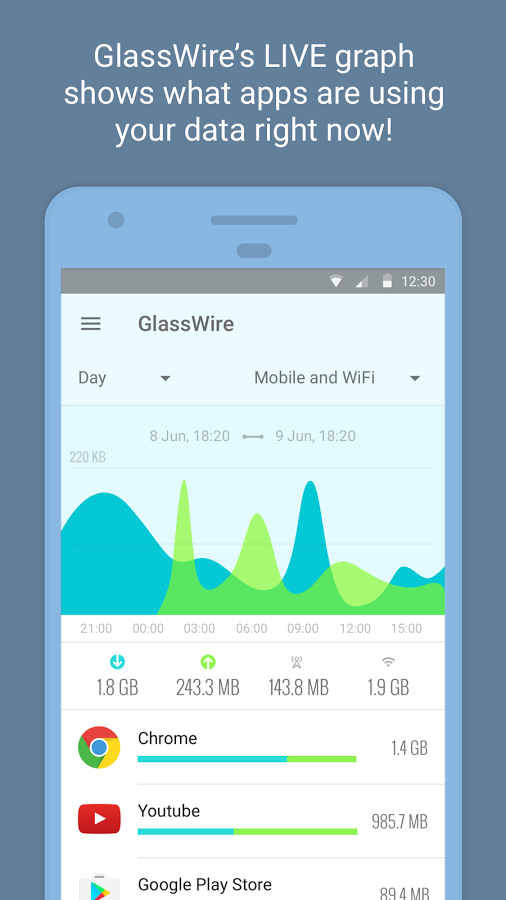
GlassWire Data Usage Monitor
Instantly see which apps are wasting your data, acting suspiciously, slowing your phones Internet speed, or causing you to go over your carrier data limits. GlassWire makes it easy to keep track of your mobile carrier data usage and WiFi Internet.
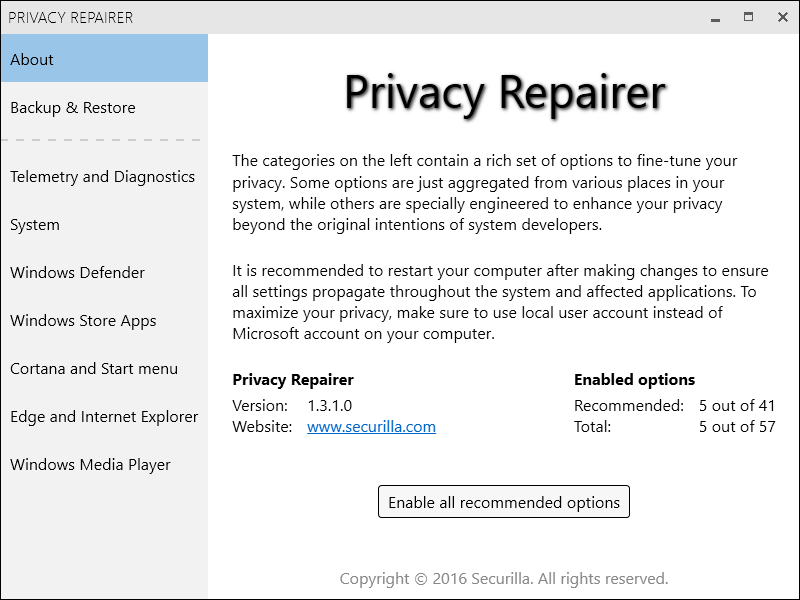
Privacy Repairer
Stop spying and surveillance in Windows 10 using our free privacy restoring software. Comes packed with almost 60 options engineered to carefully modify your system in a way most beneficial for your privacy. Perfect one click solution for most users.
SUPERAntiSpyware Professional Edition
SUPERAntiSpyware is the most thorough scanner on the market. Our Multi-Dimensional Scanning and Process Interrogation Technology will detect the spyware, adware, trojans, ransomware, malware, and infections other products miss!
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .