Block WebCam and microphone - 2.1.0.4
 How to Block WebCam and microphone ?
How to Block WebCam and microphone ?
It is becoming a problem to steal your privacy by illegally hacking your webcam or microphone.
You can use the webcam cover, but you can forget the cover after using WebCam, and there is no alternative way to prevent microphone hacking.
There is another way.
Please try 'Block Webcam and microphone'. You no longer need to use the webcam cover.
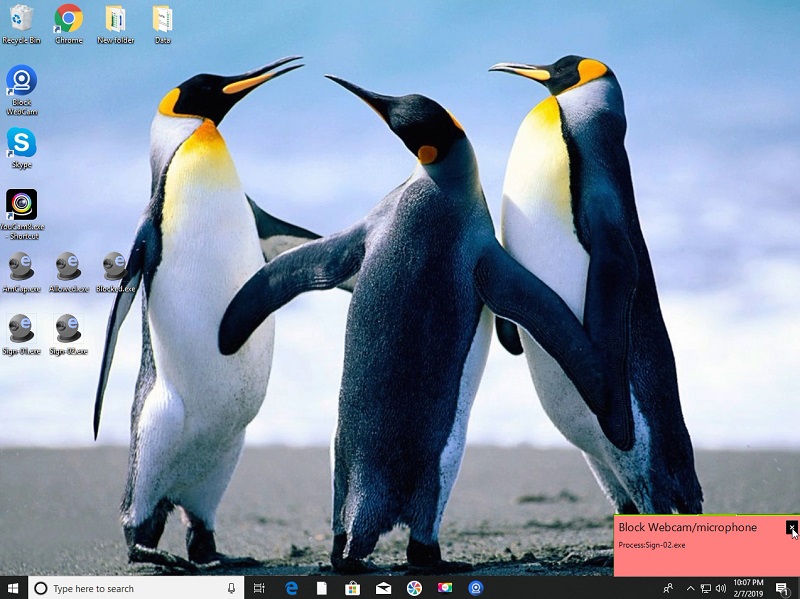
Approved programs (such as Skype, Viber) can use WebCam and Microphone, but unapproved programs can not use WebCam. If some programs access your WebCam or microphone, then you will first see a pop-up window asking you to confirm your approval. You only allow use of WebCam or Microphone for programs you trust.
You can protect your WebCam and microphone from hacking with very simple settings.
Features
* Prevent malicious programs use of WebCam or Microphone to access information.
* You must specify the applications that can use the WebCam, Microphone.
* We provide a list of widely used applications for user convenience. (Please register the accepted application easily with a single click)
* The application that is installed by default when installing Microsoft Windows can use the WebCam, Microphone.
* If an unregistered application attempts to access to webcam or microphone, ask the user whether to allow the this operation.
* When the main program is terminated, all programs can not access the WebCam or microphone.
Related Videos
* Quick Guide: https://youtu.be/090U2Soy0Ks
* Tutorial: https://youtu.be/Rqt8efpyWZM
* See more videos: https://www.youtube.com/channel/UCW9UHqHn07a5Tk_L2bmsXyw
Operating System
* Windows 7 / 8 / 8.1 / 10
* Windows Server 2008 R2 / 2012 / 2016 / 2019
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .