
Copy Protect PDF Plugin for WordPress
This plugin enables the ion of CopySafe PDF documents into WordPress posts and pages from the WordPress page editor. Without this module adding HTML to activate a browser plugin would be an arduous task, even for experienced web developers.

Copy Protect Video Plugin for WordPress
This plugin enables the ion of CopySafe Video files into WordPress posts and pages from the WordPress page editor. Without this module adding HTML to activate a browser plugin would be an arduous task, even for experienced web developers.
Copysafe PDF Protector
CopySafe PDF provides the most secure copy protection for eBook and PDF documents with the option of preventing sharing and expiry by hours or days from first use. Ideal for secure distribution by email, download, CD or displayed on your web page.

Guest Video Plugin for WordPress
Add copy protection to WordPress pages for images, PDF and video. Safe from all copy, save and exploit including sceenshots and recording.
PDF Anti-Copy
PDF Anti-Copy is a free PDF security utility that prevents PDF content from copying and ing to editable formats. After processed by this tool, your important PDF content could be viewed, but will never be copied and ed to editable files
PDF Page Lock
PDF Page Lock enables users to lock or hide selected pages of a PDF document with a password encryption. With PDF Page Lock, users could hide or lock selected pages of a PDF file while leaving all other pages available.
PDF Postman
With PDF Postman, you can send secure Outlook email messages in a manner that is easy for recipients to receive on any device. The PDF Postman add-in uses the strong AES-256 bit encryption in the PDF specification. Try it free for 15 days!
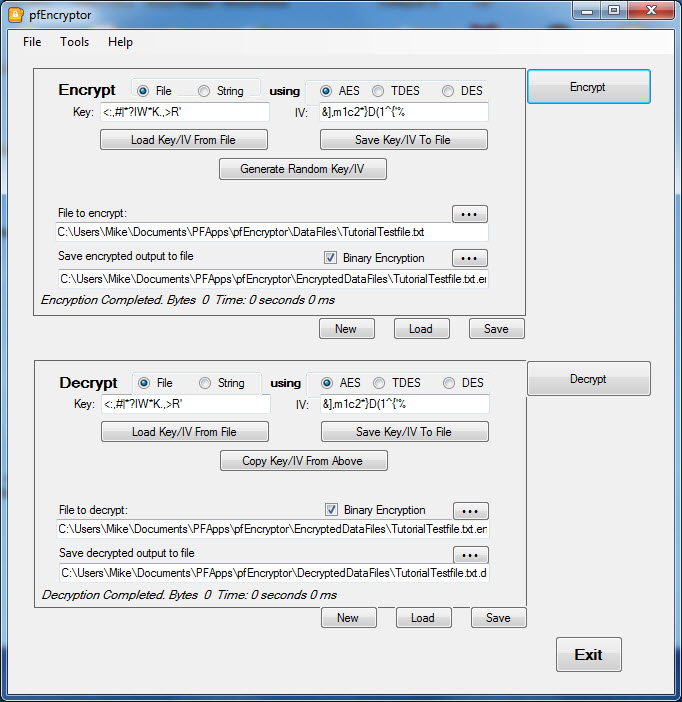
pfEncryptor
Provides interactive UI for defining and managing encryption tasks. Supports AES, TripleDES, and DES encryption standards. Can encrypt either files or standalone strings. Encryptions can either be to binary or base64 Text encoding.
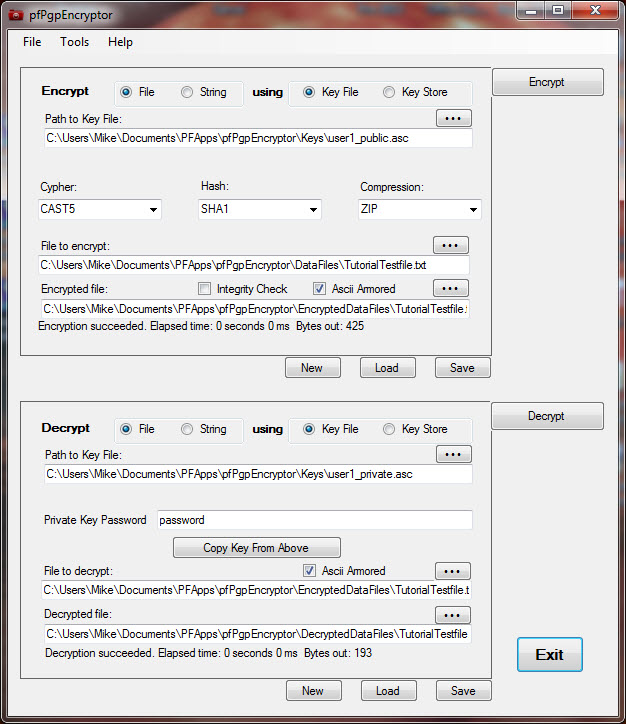
pfPgpEncryptor
Provides interactive UI for defining and managing PGP encryption tasks. Supports a wide range of cipher, hash and compression standards. Can encrypt either files or standalone text. Encryptions can either be to binary or Armored text.





