COVERT Pro - 3.0.0.18
 COVERT Pro - an innovative solution to ensure total privacy while working at the computer.
COVERT Pro - an innovative solution to ensure total privacy while working at the computer.
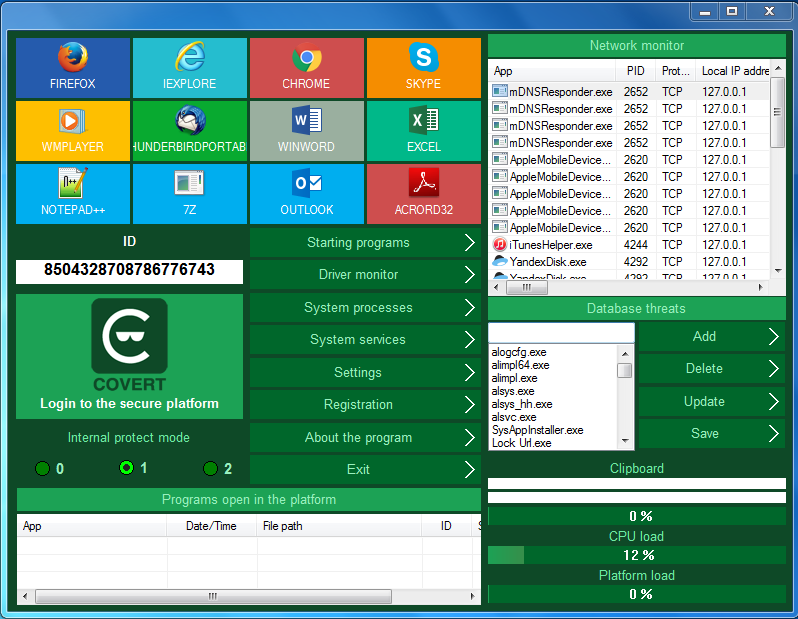
Protecting against spyware programs by masking action of computer user. Its essence is to create a secure platform in which any user can run their applications, while remaining invisible to the spies. COVERT Pro blocks reading the keyboard input and monitor screen and allows you to see all system drivers, active processes and system services to detect and remove all hidden applications.
Program has the opportunity to work with virtual keyboard and is effective on Windows tablets.
- Perpetual license. No need to pay for an annual subscription.
- Free upgrade to new versions.
- Effective even on infected computer.
- With a single USB-version, you can protect all your computers and tablets with Windows.
- COVERT Pro saves your time because you do not need to scan your hard drive.
- COVERT Pro does not require access to the Internet to create a secure platform.
- COVERT Pro is compatible with any antivirus.
Traditional antivirus and antispyware software does not protect against many of screenshoters and keyloggers, because this action is not prohibited, as it is unknown - does that make user himself or someone is spying on him.
Search for unknown spyware on the hard drive is ineffective because they are not in the databases of malware. Analysis or study of the behavior of code is also meaningless, since it is not known who and for what purpose performs actions that are typical for spies.
Therefore, the traditional antivirus software will not protect you against spyware and riskware.
COVERT Pro gives you something that is natural for each of us - the right to privacy in cyberspace. You have a right to ensure that your information would be unavailable to others without your permission. It does not matter who it is - a relative, your friend, colleague, or a stranger.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .