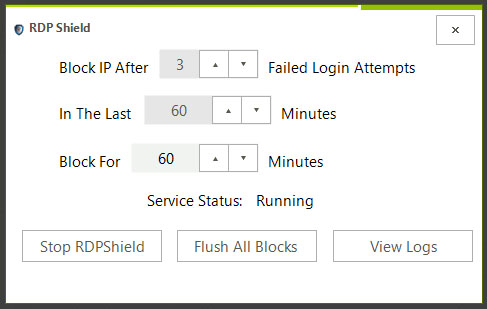
RDP Shield
Protect your server or PC from brute force attacks via remote desktop. Automatically block IPs that pass incorrect login credentials.
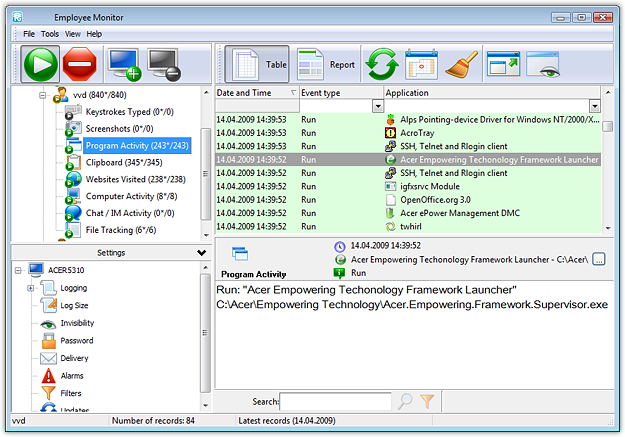
REFOG Terminal Monitor
A surveillance software to monitor employee activities on the Terminal Server, prevent security breaks and control how much time employees spend for work and for leisure. Allows administrators to track user compliance to company policies.

RusRoute firewall
RusRoute (routing firewall, Internet gateway) is for making Internet gateway for local area network (LAN) of some firm, encountering and restriction of the traffic of users, protection against of network attacks with functions of NAT, VPN, proxy.
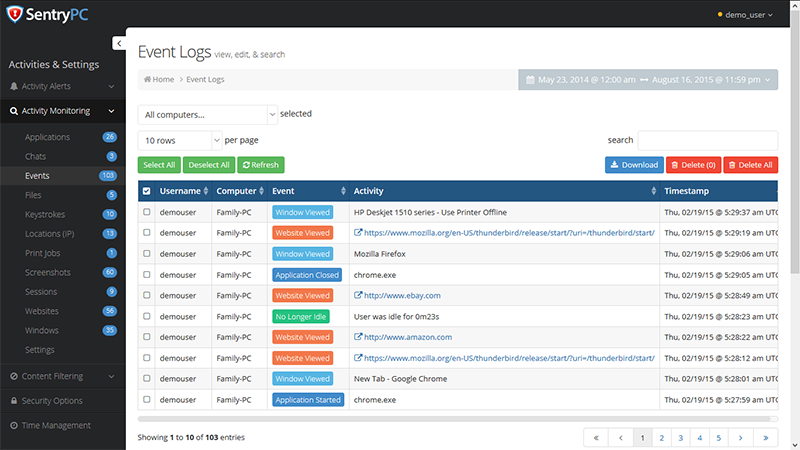
SentryPC
SentryPC is an all-in-one computer monitoring, content filtering, and time management software solution. Entirely cloud-based, you can monitor and control any number of computers, and their users, remotely from anywhere in the world.
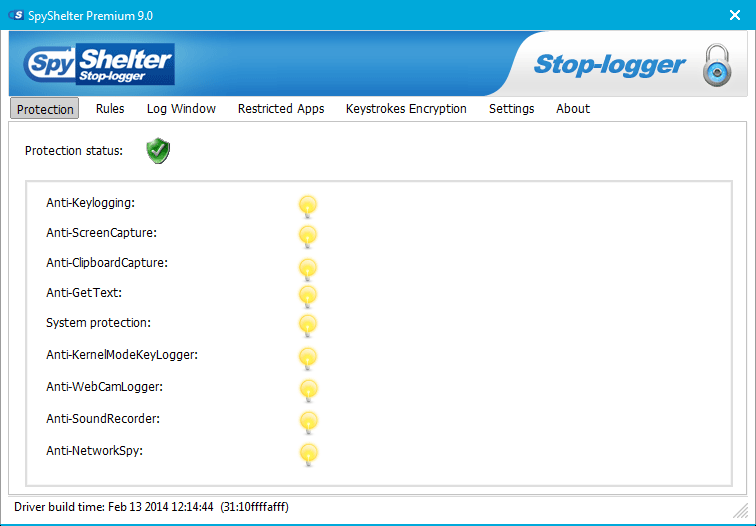
SpyShelter Premium
SpyShelter Premium monitors susceptible and weak spots in your computer system, in order to ensure that even the most advanced keyloggers are shut down even before these can launch a single dangerous attack against your computer.
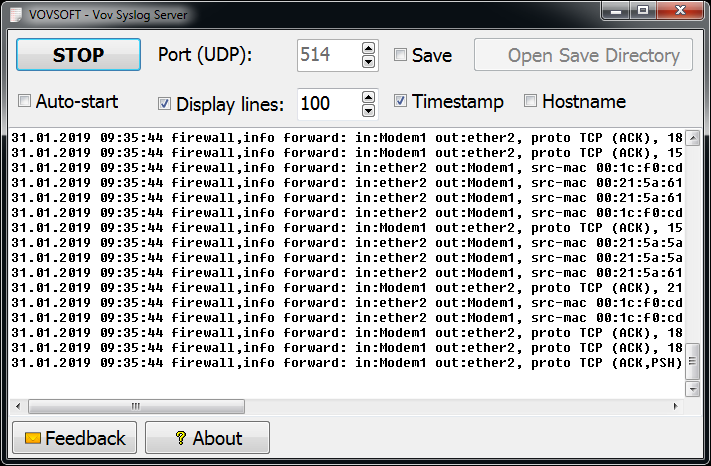
Vov Syslog Server
View and archive syslog messages in real-time. Once launched, the application is ready to start monitoring messages coming to your computer. The program automatically reads necessary info.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .