RDP Shield Brute Force Protection for Remote Desktop
Author: Will Kruss
Dated: 2019-08-24
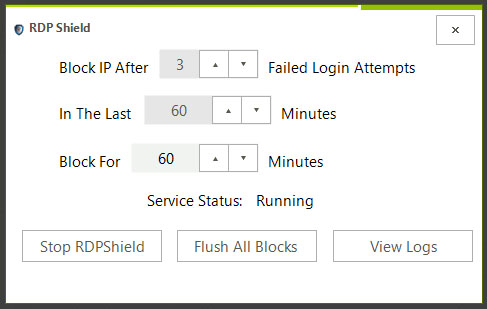
RDP Shield monitors remote desktop connections and in particular failed login attempts, and blocks an IP when an attack is suspected.
 12 Sep 2014 -- VPSBlocks today announced the release of version 1.0 of RDP Shield, remote desktop brute force protection software.
12 Sep 2014 -- VPSBlocks today announced the release of version 1.0 of RDP Shield, remote desktop brute force protection software.
RDP Shield monitors remote desktop connections and in particular failed login attempts, and blocks an IP when an attack is suspected. It allows the user to configure the number of failures within a certain time to indicate an attack, as well as the amount of time to block an attacker.t
RDP Shield runs as a service and starts automatically when your server or computer restarts. A handy configuration tool sits in the system tray, where you can monitor the service, flush existing blocks and view logs. RDP Shield is a must have for any server or computer with a publically available remote desktop server.
With remote desktop brute force attacks on the rise, and many articles written on the subject in 2014, with no built in support provided by Microsoft, and only paid programs available to perform this relatively simple task. VPSBlocks started developing RDP Shield to install on their clients systems, and decided to release it as freeware to the wider community in the interests of internet security.
Shield is completely 100% free.
RDP Shield is available now, and may be downloaded through our web site.
VPSBlocks is one of Australia's leading VPS providers, founded in 2012 it has quickly become the go to place for 100% SSD and high availability services within Australia. VPSBlocks distributes RDP Shield 'as-is', without any express or implied warranty. In no event will the authors be held liable for any damages arising from the use of this software.
For more info see related reference at RDP Shield Brute Force Protection for Remote Desktop
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .