Desktop Secret Lock - 1.0.0.6
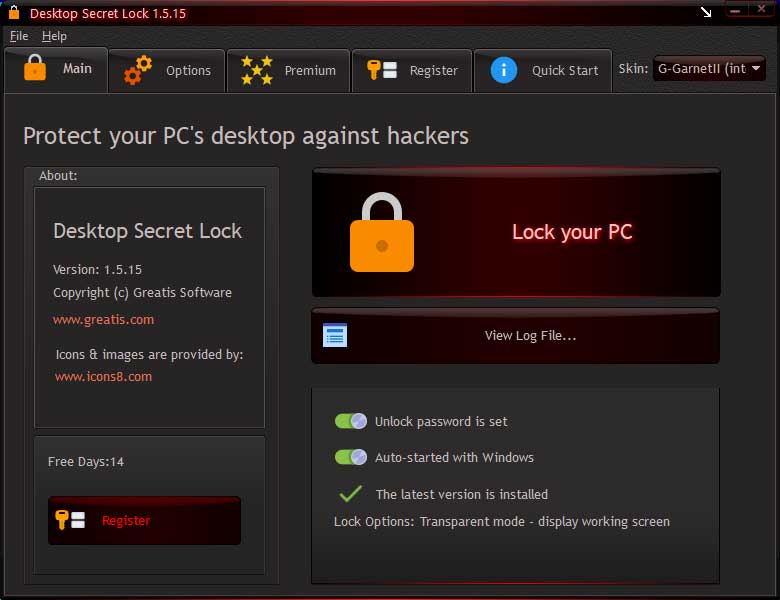 Desktop Secret Lock adds an additional level of security to your computer or remote desktop server.
Desktop Secret Lock adds an additional level of security to your computer or remote desktop server.
For home or office PC: you will know if anyone makes a mouse click or presses any key on your PC.
For remote server: if you use Windows RemoteDesktop/TeamViewer/Anydesk software for remote control, your system is under risk! Hackers may use vulnerabilities in Remote Desktop software or discover a password through a brute-force attack.
Desktop Secret Lock uses a non-standard locking method for enhanced security, and its own unique password which is separate from your computer's password.
A locked computer looks like it's unlocked, but it is in a mode which securely prevents anyone from accessing the working desktop.
You will be notified if someone has clicked on your desktop or pressed any key in your absence.
Features:
1) Transparent Desktop Lock.
A locked desktop looks like the everyday, unlocked desktop, ready to be used.
If anyone makes a mouse click or presses any key when in locked mode, the response will be an invitation to unlock the desktop using the owner-set password. Desktop Secret Lock will write all these events to its log file.
2) Secure Lock.
Desktop Secret Lock creates its own desktop and displays it instead of your normal Windows desktop. There is no way to get back to the normal desktop without entering the correct password.
3) Auto Lock
-Desktop Secret Lock can lock the desktop by use of a shortcut key, or by specifying a certain period of inactivity.
- Auto lock at Windows startup.
- Auto lock if a reboot is initiated without first unlocking the desktop.
- Auto lock at a specified time.
4) Safety Unlock using USB flash stick
Desktop Secret Lock has an option: 'Saving key file to USB flash stick'. This feature is useful if you forgot your password. Just insert your flash stick into USB port of your PC and it will be unlocked.
5) Log Journal.
All mouse clicks and key presses are logged.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .








