Spy DLL Remover - 7.0
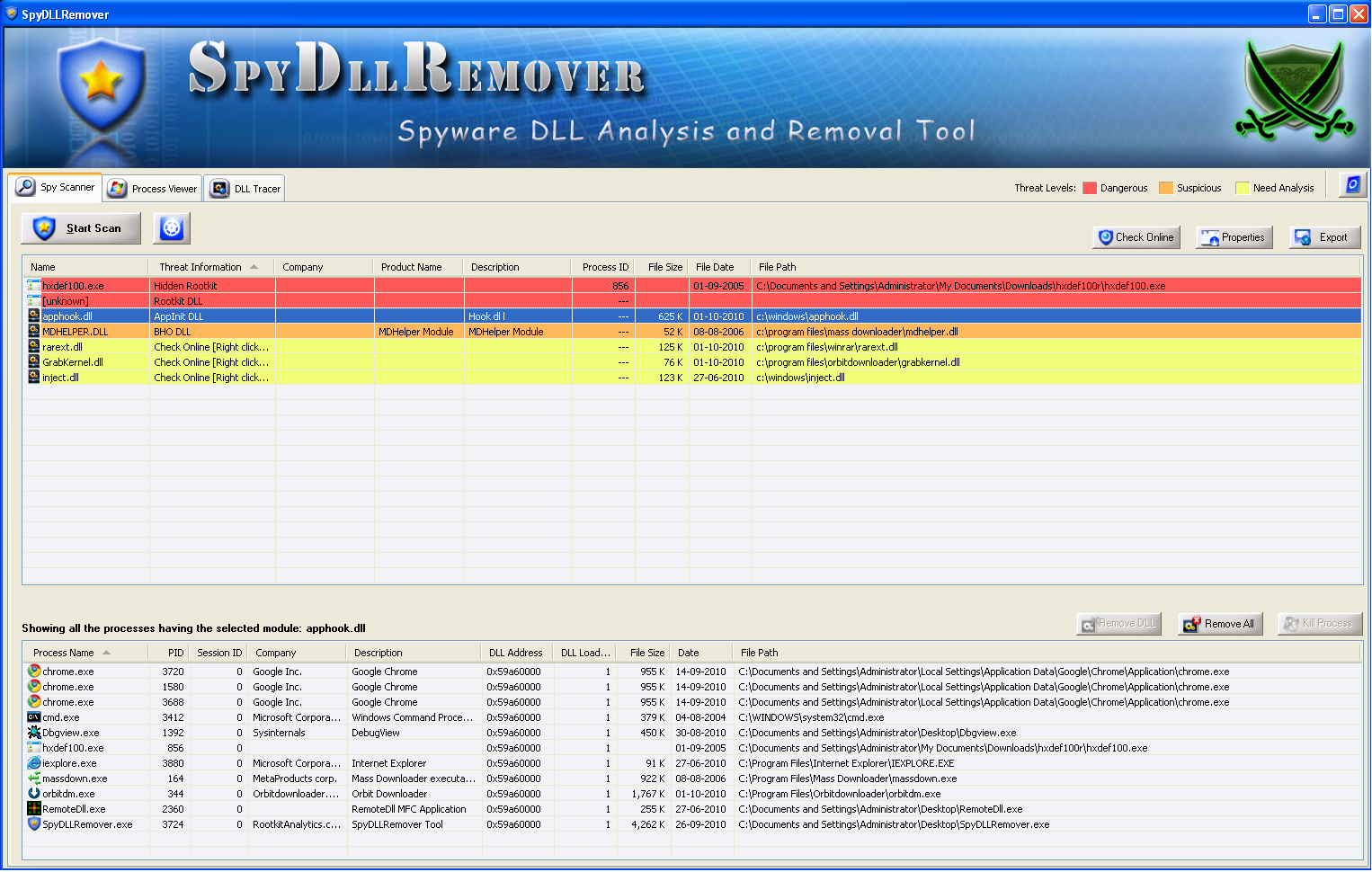 SpyDllRemover is the specialized tool for detecting Spyware & Hidden Rootkit Dlls in the System.
SpyDllRemover is the specialized tool for detecting Spyware & Hidden Rootkit Dlls in the System.
In addition to Spyware Dlls, it can also detect user-land Rootkit processes using multiple Anti-Rootkit techniques. It uses Heuristic analysis and 'Online Threat Verification' for deeper analysis of unknown Malware Threats.
One of the unique feature of SpyDllRemover is 'Advanced Dll Ejection' which helps in completely removing Spyware/Rootkit Dlls from any running Process remotely.
Here are the key features
# Advanced Spyware Scanner: Detects Hidden User-land Rootkit processes as well as suspicious/injected Dlls within running Processes.
# Hidden Rootkit Detection & Removal: Uses multiple Anti-Rootkit techniques to detect user-land Rootkits
# Unique 'Advanced DLL Ejection': This is one of the Advanced & Unique feature of SpyDLLRemover used to completely remove the injected DLL from Remote Process.
# Sophisticated Auto Analysis: Dll & Process Heuristics to help in Identification of known as well as Unknown Threats.
# Color based Representation: For clear and easier analysis of various type of Spyware Threats.
# Online Threat Verification: Scan suspicious Processes/DLLs using online services such as VirusTotal, ThreatExpert, ProcessLibrary and Google.
# 'DLL Tracer' Feature: Search for suspicious DLL within all running processes.
# Cooler GUI Interface: Attractive, Easy to Use & Customizable interface.
# Advanced Report: Generates complete report of Processes/Dlls along with Threat Analysis.
SpyDllRemover is fully Portable software and works on wide range of platforms starting from Windows XP to Windows 10
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .








