Secure IT Encryption Software - 12.2.0.0
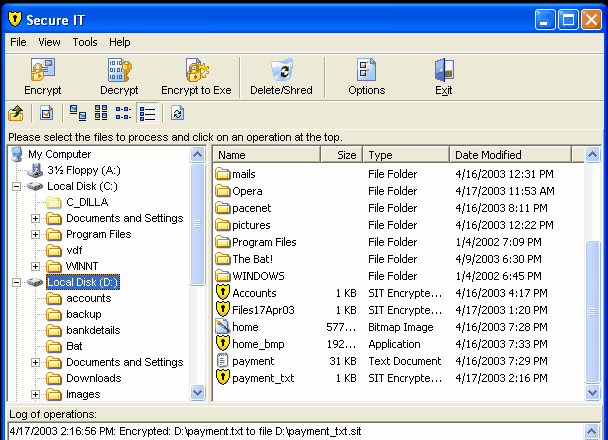 Cypherix's Secure IT File and Folder Encryption Software is an easy to use, feature packed program that protects all your files and folders using 448-bit strong Blowfish encryption. It includes a powerful, customizable file shredder. Secure IT File Encryption Software has the ability to generate self-decrypting email attachments that allows the user to send encrypted/secure email to anyone - the recipient need not have a copy of the program. This strong encryption software ensures that it is statistically impossible for an unauthorized person to access the encrypted data. SIT 2000 is so simple to use. SIT 2000 is designed to meet the growing security and privacy needs of all computer users. The software combines ease of use with state of the art technology to ensure total security with a zero learning curve and maximum convenience. The program is fast, and requires relatively few computing resources and little time to encrypt files. The software provides full access control. No unauthorized access to encrypted data is possible under any circumstances, i.e. there are no 'back doors'. It ensures encryption of every type of file such as spreadsheet, graphic, or word processor. The software works on any kind of medium, whether floppy disk, removable hard drive, zip drive or tape drive. Secure IT 2000 is transparent to the end user, designed to hide the complexities of encryption technology from the end user. It runs on all 32-bit as well as 64-bit versions of Microsoft Windows (Windows XP, Vista, Windows 7, Windows 8 as well as Windows 10).
Cypherix's Secure IT File and Folder Encryption Software is an easy to use, feature packed program that protects all your files and folders using 448-bit strong Blowfish encryption. It includes a powerful, customizable file shredder. Secure IT File Encryption Software has the ability to generate self-decrypting email attachments that allows the user to send encrypted/secure email to anyone - the recipient need not have a copy of the program. This strong encryption software ensures that it is statistically impossible for an unauthorized person to access the encrypted data. SIT 2000 is so simple to use. SIT 2000 is designed to meet the growing security and privacy needs of all computer users. The software combines ease of use with state of the art technology to ensure total security with a zero learning curve and maximum convenience. The program is fast, and requires relatively few computing resources and little time to encrypt files. The software provides full access control. No unauthorized access to encrypted data is possible under any circumstances, i.e. there are no 'back doors'. It ensures encryption of every type of file such as spreadsheet, graphic, or word processor. The software works on any kind of medium, whether floppy disk, removable hard drive, zip drive or tape drive. Secure IT 2000 is transparent to the end user, designed to hide the complexities of encryption technology from the end user. It runs on all 32-bit as well as 64-bit versions of Microsoft Windows (Windows XP, Vista, Windows 7, Windows 8 as well as Windows 10).
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .








