Computer Monitor - 4.9
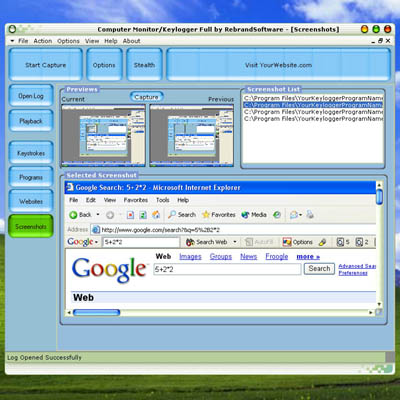 Secretly monitor all activity on your computer, capturing keystrokes, programs, internet explorer websites and screenshots.
Secretly monitor all activity on your computer, capturing keystrokes, programs, internet explorer websites and screenshots.
Completely invisible and easy to use, all information captured is stored in an encrypted log file. The log file can be sent secretly at scheduled intervals to any specified email address.
All activity in Internet Explorer can be monitored, and webpages are cached for viewing offline.
Screenshots can be taken at given intervals, capturing everything that is currently on the screen.
Monitor your computer while you are away, retrieve lost information, monitor your childrens activity, and much more!
Capture keystrokes, even passwords!
Capture programs used
Capture websites in Internet Explorer
Capture screenshots
Encrypted log file
Secretly email log files
Invisible Stealth Mode
Unique playback mode lets you view captured keystrokes/programs/webpages/screenshots in real time
Run silently at startup
Auto-capture at startup
Does not Contain any Adware, Spyware, or other Third Party Software.
A brandable (a.k.a. Private Label) version of this software, with full resell rights, is available at www.rebrandsoftware.com.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .








