Blacklist Exortion Scam
UCEPROTECT, an online spam reporter well known for its attempts to extort payment for delisting, targets large networks to entrap clients found within their netblocks.

DRM & Copy Protected Protected File Hosting
Guest Video is the first only file hosting service that provides options for DRM, copy protection and watermarking for web pages, and media including images, PDF and video.

The Best Copy Protection for WordPress Websites
The SafeGuard Media plugin for WordPress provides unmatched copy protection from all methods of copy by creating a secure tunnel between the web server and the user*s desktop.

The Fate of Shareware Promotion
Much of what supported the free software industry has been eroded by search engines mercilessly classifying software and shareware review services as spam advertisers.

How Spam Blocklists Can Be Useless
While network admins may be using what they think are honorable spam reporting services, some are targeting large networks to trap their clients and extorting payment for removal from their blocklist.
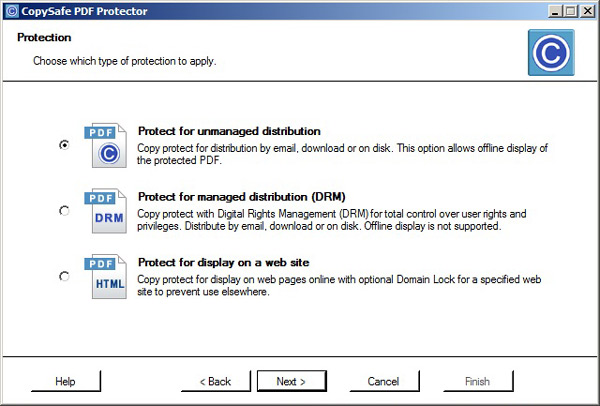
How To Manage Document Rights for PDF
CopySafe PDF Protector has the capability of managing document rights access from your own web site. CopySafe PDF Protector can be bundled with add-ons for management of DRM on your server.
Most Secure Site Protection
ArtistScope launches the most secure web site protection system for copy protecting web pages, images, html, source code, Flash, movies, PDF and database records without data leakage and other exploits enabled by modern web browsers.
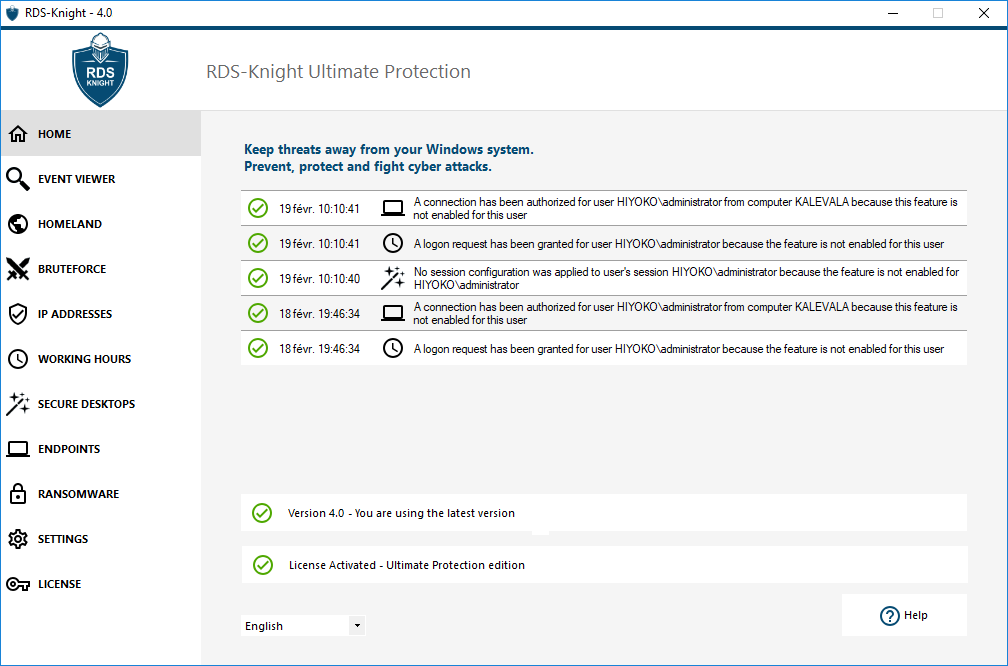
RDS-Knight Server Security
This update improves two of the core features that protect Remote Access Servers against unauthorized access.
Secure Hunter Anti-Malware
Secure Hunter, a renowned name when it comes to providing Cyber Security Solutions has announced the release of their Secure Hunter Anti-Malware