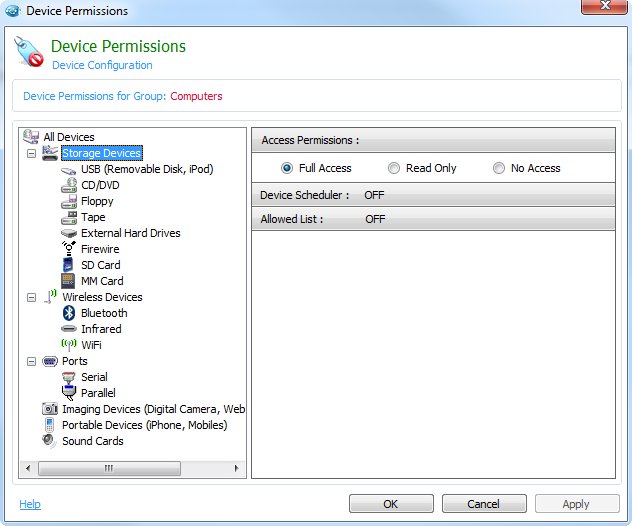
AccessPatrol
AccessPatrol provides a proactive solution for securing endpoints (USBs, CDs/DVDs, BlueTooth, WiFi, iPods, MP3s) to prevent illicit transfer of data to unauthorized devices.
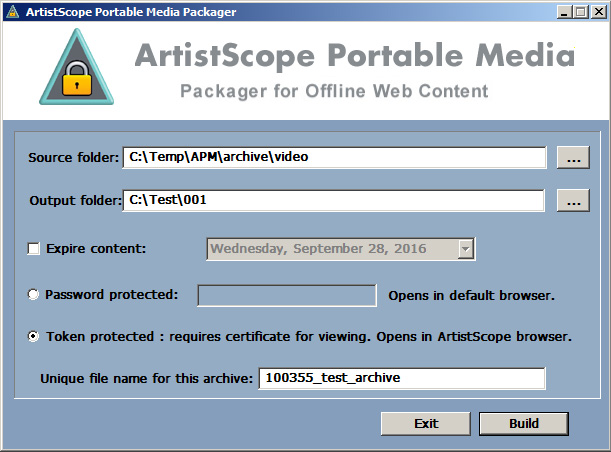
ArtistScope Portable Media
ArtistScope Portable Media (APM) enables the distribution of most types of media by email, download or CD/USB for local viewing (while offline). Media archives can be distributed for viewing and protected by password, or DRM with access tokens.
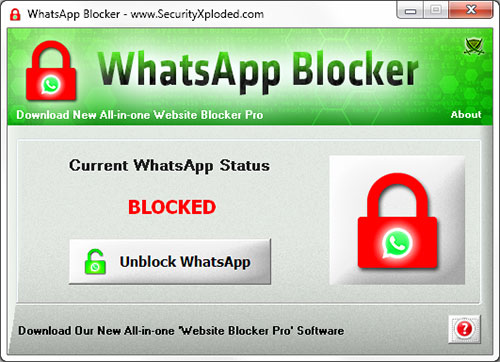
Block WhatsApp
free tool to quickly Block WhatsApp on your Windows computer from all web browsers & WhatsApp application.

Desktop Secret Lock
Desktop Secret Lock adds an additional level of security to your computer or remote desktop server. You will be notified if someone has clicked on your desktop on your desktop or pressed any key in your absence.
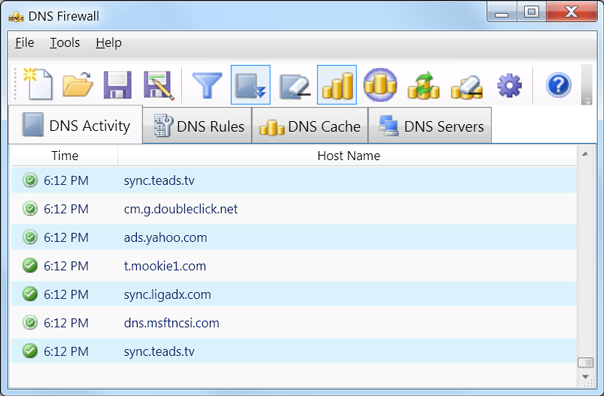
DNS Firewall
This easy to use DNS Firewall has flexible rules for domain name blocking. It has DNS activity log for DNS traffic monitoring. It maintains it own DNS cache for faster web browsing. It has Exclusive DNS cache mode for using only local DNS cache.
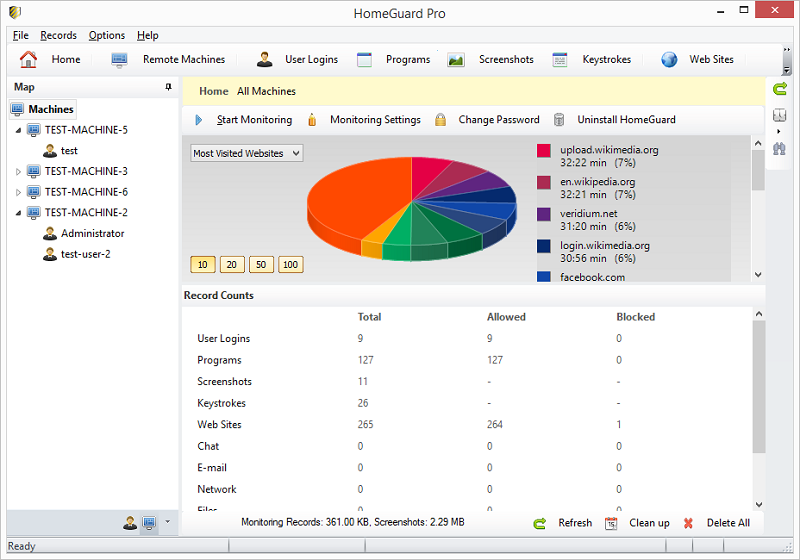
HomeGuard Professional
HomeGuard professional is an easy to use software with extensive monitoring and blocking features for tracking and controlling the use of computers in home and office networks. Features include a website filter, program blocker, keylogger...and more.
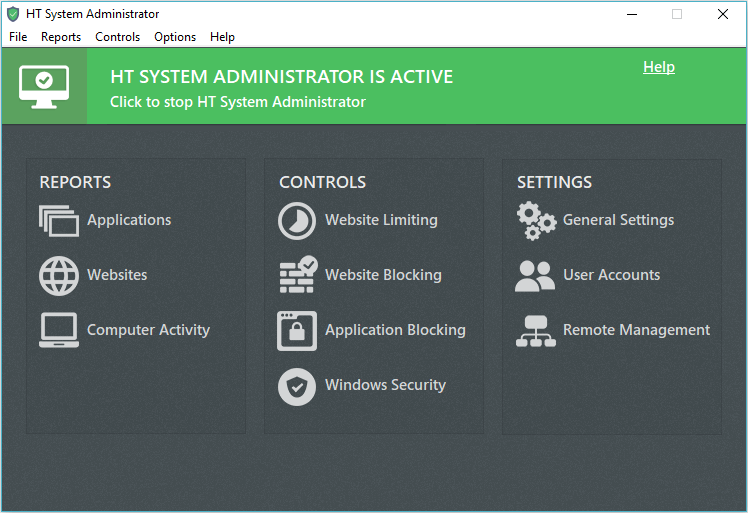
HT System Administrator
Block unwanted computer activities and increase productivity as simply as possible. With HT System Administrator, block any websites/applications and view reports of computer use in a few clicks.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .